41. Can you list some of the popular consensus algorithms? Why we need different consensus mechanisms?
Some of the popular consensus algorithms are:
• PBFT (Practical Byzantine Fault Tolerance)
• Proof-of-work
• Proof-of-stake
• Delegated proof-of-stake
• Proof-of-elapsed time
Now, the possible reasons why we need consensus mechanism more than “proof-of-work” are”
• Different business needs
• Different use cases
• Also:
• Cryptography/Strength of Algorithm
• Regulation requirements
• Implementation
• Performance
• Tokenization
• Security
• Privacy
42. Is there any network specific conditions for using Blockchain technology in an organization?
There is no specific condition of using it. However, the network must be a peer-to-peer network under the concerned protocols. It validates the new block simply and helps organizations to keep up the pace in this matter without investing in third-party applications.
43. How useful is blockchain to digital protection and cybersecurity?
Blockchain is an anti-tamper solution that can help data-sensitive information to be protected. This means that blockchain can be useful to both cybersecurity and digital protection. Other key features of blockchain that helps it to provide value to digital protection and cybersecurity are transparency, integrity, and a decentralized approach. Cryptography is also used in blockchain which also protects data and improves cybersecurity.
44. What is Metamask?
Metamask is a web app that lets you connect with Ethereum dApps directly from your browser. This means that you don’t need to have a full Ethereum node to access dApps and its functionalities.
45. Name the steps that are involved in the Blockchain project implementation?
Well, there are total six steps involved in this process and they are:
1. Requirement identification
2. Screen ideas consideration
3. Project development for Blockchain
4. Feasible study on the security
5. Implementation
6. Controlling and monitoring the project
BLOCK CHAIN TRAINING
Weekend / Weekday Batch
46. How the security of a block is maintained?
The security of the blocks is kept by connecting each block to the previous one using hash identifiers. This means that the block data cannot be changed or altered as the hash value will change. Moreover, each data stored in a block is also protected using cryptography. The data can be unlocked by the network participant who created it in the first place. The private key is required to access the data. The transactions that are stored in a block is digital signed and hence once stored cannot be altered, giving the block the required integrity and transparency when needed.
47. What is double spending?
Double spending is the process of spending the same digital currency twice without the network security noticing it. Double spending is one of the biggest problems in the market, and the financial institution takes extra caution to ensure that they prevent double spending at any cost. It is mainly done by duping the network to think that the original amount is never spent, making it available to be used for other transaction.
48. How double spending can be stopped in a blockchain?
Double spending is prevented by blockchain with the help of the consensus algorithm. The consensus algorithm ensures that the transaction is genuine and records it in the block. It is thus verified by multiple nodes making double spending possible. However, 51% network attack can make any blockchain vulnerable to double spending as more than 50% of the network is controlled by one entity.
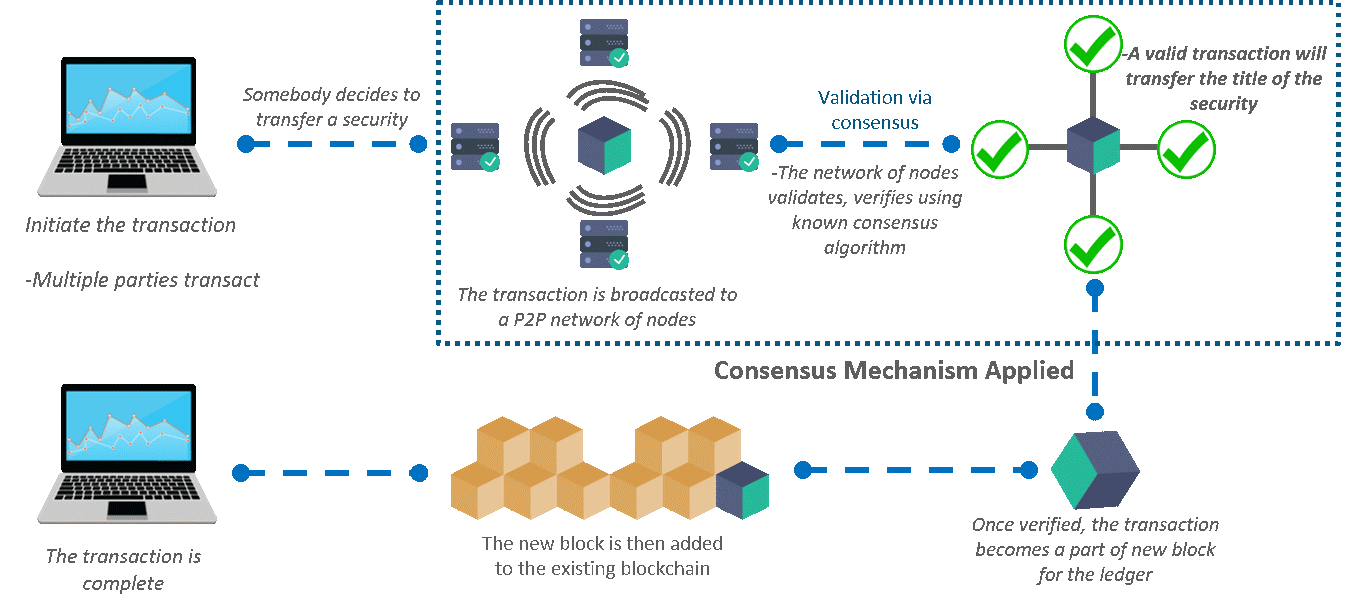
49. Explain a real-life use-case where Blockchain is being used?
Blockchain in Stock Market
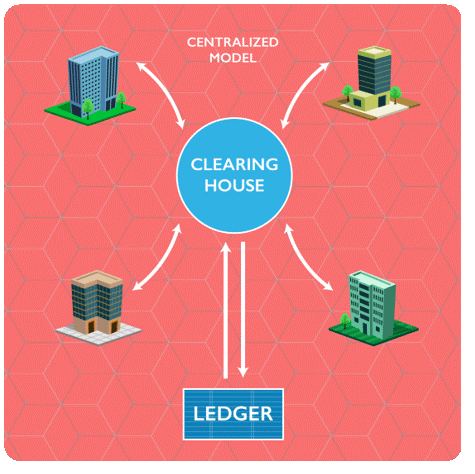
Problems in Present Stock Market:
Centralized and expensive
• Depositories and transfer agents are a single point of failure
• Registration, transfer, distribution, scrutineering, courier fees
• The more widely held, the higher the administration costs
Limited Transparency
• Information asymmetry leads to market advantages
• Forged securities still a concern
• Counterparty risk is systemic
50.How Blockchain solves the problem
The centralized hub can be removed and the blockchain can be used to directly transfer share ownership between investors.
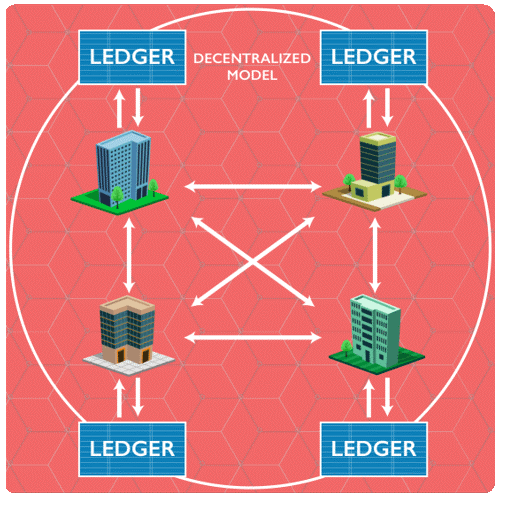
A ledger updated in minutes could save millions in collateral and settlement costs, while also automating banks’ creaky and expensive back office systems.